Identity Protection
for Microsoft 365

Did you know that email is the starting point for 91% of cyberattacks? 1
Understanding The Threat of BEC
BEC (Business Email Compromise) is one term that demands attention in cybersecurity. This cybercrime involves scammers/threat actors adopting the digital identity of a trusted persona, to manipulate employees or customers into taking actions that serve the threat actor’s agenda.
These actions could range from unauthorised payments and purchases to sharing sensitive data or disclosing confidential information.
BEC attacks are cunning, relying on social engineering techniques, exploiting weak authentication credentials, or capitalising on users’ inclination to approve Multi-Factor Authentication (MFA) prompts. Unfortunately, these attacks often go unnoticed and slip past traditional security tools and spam filters.
Ask Yourself
How Can We Help Protect Your Business?
Having seen this first-hand and understanding the gravity of this threat, we offer a Managed Detection and Response (MDR) solution as part of our robust security services. Adding a layer of protection to your Microsoft 365 cloud identities and applications, against BEC threats.

Suspicious logins
User login credentials are comprised or the user has approved a malicious MFA prompt.

Shadow Workflows
We look for dodgy inbox rules, watching for unexpected email redirects, in addition to historical rules already in place.
Rogue Microsoft 365 Apps
Malicious application installs or weaponising legitimate applications to exfiltrate data and establish persistence
Session Hijacking
We look for specific behaviour associated with stealing login tokens, which can bypass Multi-Factor Authentication.
Why Choose Our Solution?
By detecting and responding to suspicious user activity, permission changes, unusual mailbox rules and anomalous access behaviour, and backed by a 24/7 SOC (Security Operations Center) team, our solution empowers us to fight back against attackers on your behalf.
By taking a proactive stance, we minimise the risk of your business falling victim to BEC incidents.
Protect your business today!
Some Common Threats
We Look For
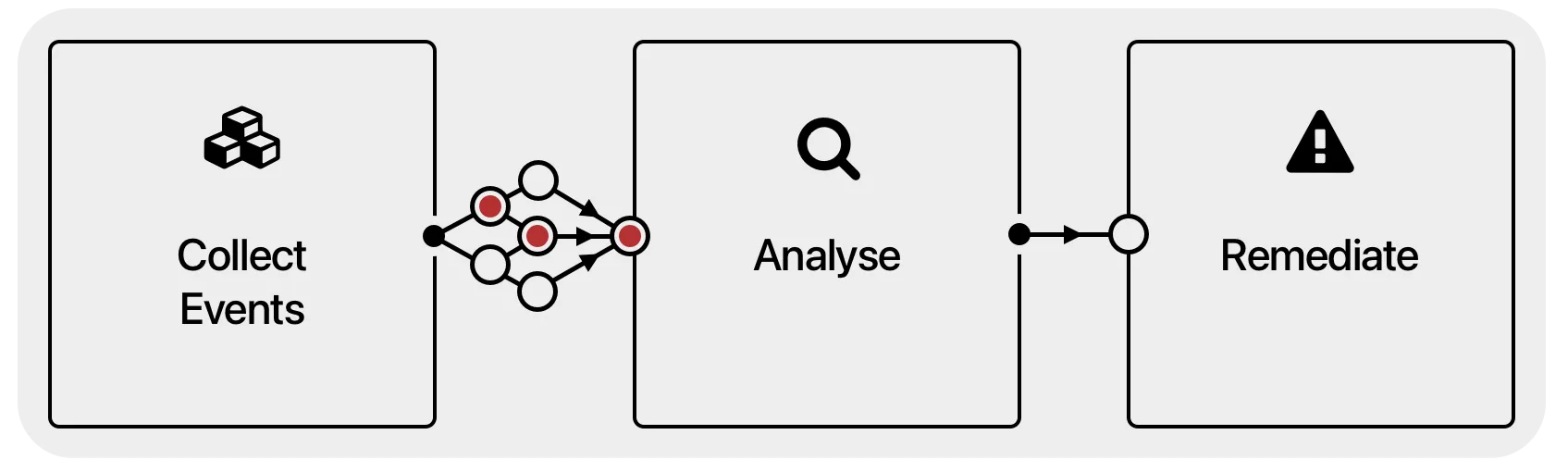
How it works
- Source: “Protecting against coronavirus themed phishing attacks”. Microsoft Security blog. March 20, 2020. ↩︎

